SECURITY
-
Summitas employs a variety of measures designed to ensure private information stored in your digital vault is safe from prying eyes, but you also have an important role to play in keeping your information confidential. Here's what you can do:
- Keep your security information (Login ID and Password, challenge questions and answers, and document passphrases) in a secure place that cannot be compromised. Storing the information in a human readable form on your computer is not advisable.
- Make sure you have a frequently updated anti-virus program running on the computers you use to access Summitas. Make sure your computers are free of existing viruses and hidden programs like keystroke loggers (a keystroke logger records everything the user types and stealthily sends the information via hidden email to the criminal).
- Do not share your security information via unencrypted email (we recommend you place a phone call or share the information in person).
The following steps have been taken by Summitas to ensure only you, and those you appoint, can gain access to information stored in your digital vault:
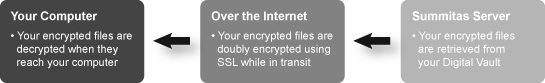
- Documents stored at Summitas are encrypted on YOUR computer utilizing state-of-the-art encryption standards BEFORE being uploaded to Summitas for storage in you digital vault. When you want to read a document in your vault, the encrypted file is decrypted AFTER being downloaded to YOUR computer.
- Encrypting files on your computer adds an additional measure of security. Why? A common practice of websites is to encrypt clear text (human readable) files using the Secure Sockets Layer (SSL) protocol while in transit between your computer and the Web server (you know you are using SSL when the URL in your browser's address bar begins with https://). SSL encrypts data while it traverses the Internet and automatically decrypts it when it arrives at the destination. While this is the approach used by most websites for credit card transactions and the handling of personal identifiable information, it introduces a potential weakness for files that must remain encrypted in storage, like those in your digital vault. The potential risk arises from the fact there's a brief moment when the clear text file is readable on the server after being decrypted by SSL and prior to being re-encrypted by the servers' encryption software. That brief moment when the file is readable on the server provides an opening for criminal attacks. The Summitas approach ensures your information is encrypted at all times after it leaves your computer.
- For the digital vault, Summitas uses SSL only as a second line of defense since files transiting the Internet are already encrypted locally on your computer. In effect, your files are doubly encrypted by Summitas: first locally in your computer, and second, during transmission using SSL. The major benefit of this approach is that in the unlikely event an SSL encrypted transmission is decoded, the decoded data would be encrypted and therefore useless.
Uploading Files TO Your Digital Vault

Downloading Files FROM Your Digital Vault
How it works
- There are three passphrase options providing varying degrees of security for encrypting documents stored on Summitas servers. You can select the best encryption option on a document-by-document basis.
I. Non-Recoverable: only you, and those you choose to share it with, know the passphrase. Even if a cyber criminal ("hacker") gains access to your login credentials (Login ID and Password) or manages to break into the www.summitas.com website, your encrypted documents cannot be compromised because the passphrase is known only to you and the Family Office members you share it with. Non-recoverable passphrases are NOT stored on Summitas servers so if you lose them, no one can decrypt your documents.
II. Recoverable: Summitas encrypts and stores your passphrase on Summitas servers. Even if a hacker managed to break into Summitas and was somehow able to decrypt a passphrase, your document could not be decrypted without access to your login credentials (Login ID and Password). If someone gained access to your login credentials, but did not possess your document passphrases, they would need to know the answers to at least two challenge questions in order to recover your passphrases and decrypt your documents.
III. Auto-Generated: Summitas auto-generates and encrypts a passphrase for you. Even though the documents are encrypted using the passphrase, this is the least secure option since it does not protect your documents if your login credentials (Login ID and Password) are compromised.
- The encryption mechanism Summitas employs for document encryption is known as "block cipher cryptography" and the algorithm is called the Advanced Encryption Standard (AES). AES was adopted as an encryption standard by the United States Government for managing its own secret documents and is used worldwide to protect sensitive data. The National Institute of Standards and Technology (NIST) announced its use in U.S. Federal Information Processing Standard (FIPS) Publication 197 on November 26, 2001 after a 5-year standardization process. See: http://csrc.nist.gov/publications/ for more information.
- When you ask Summitas to maintain encryption passphrases required by AES, or if you request that Summitas generate your AES passphrases for you (designated as "Recoverable" and "Auto-Generated," respectively), Summitas uses a second block cipher algorithm known as Triple DES to encrypt them on YOUR computer BEFORE transmitting them for safe storage to the Summitas site. Triple DES (Data Encryption Standard), as the name suggests, is applied three times to the same data for maximum security.
- Small programs are downloaded in real-time from Summitas to manage the encryption/decryption process. These "Java Applets" are digitally signed using a sophisticated digital certificate mechanism based on an industry standard (X.509) and provided by Digicert®, the worldwide leader in digital security for the Web. In the unlikely event a hacker was able to gain access to, and then modify a Summitas Java Applet, you would be immediately notified that the digital signature of the modified applet is invalid and that the applet should not be trusted. See www.digicert.com for more information.
- All confidential information you send to, or receive from, Summitas, including already encrypted documents, is encrypted using SSL V3 (Secure Sockets Layer) using 256-bit encryption with modern browsers or 128-bit encryption with older browsers (Summitas does not allow SSL to encrypt with less than 128-bit encryption). SSL V3 is the latest standard for encrypting sensitive information while in transit over the Internet.
Security Outside the Digital Vault
- Summitas also uses Triple DES to encrypt Family Office Private Messaging, Family Office Forums, and Family Office Calendars. Member permissions used to assign digital vault access rights do not expose personal identifiable information (PII) of the office owner or office members.
Third-party Compliance- The security techniques Summitas employs are advanced. The U.S. Government's Bureau of Industry and Security, U.S. Department of Commerce has approved Summitas' use of the technologies for the www.summitas.com website. See: http://www.bis.doc.gov/ for more information.

- The entire Summitas website is scanned on a daily basis for security vulnerabilities by TrustedSite. If TrustedSite finds a vulnerability, Summitas must correct the problem quickly or lose the TrustedSite certification. Summitas' use of TrustedSite helps keep you safe from identity theft, credit card fraud, spyware, spam, viruses, and online scams. See: https://www.trustedsite.com for more information.

- The Digicert Secured™ logo present on the Summitas website indicates the validity of the Digicert® digital certificate used to authenticate the Summitas site (thereby demonstrating that you are on the real Summitas website—make sure the URL in your browser's address bar always begins with https://www.summitas.com while on the Summitas site). The Digicert® digital certificate is also used to digitally "sign" the Java Applets used by the digital vault (indicating to you that the Java Applets are genuine; your browser should prompt you if the signed Java Applet has a digital signature mismatch). You can also verify the validity of the Summitas digital certificate by clicking on the Digicert Secured™ logo.
- The logo present on the Summitas website is awarded to companies who pass a rigorous test to ensure they employ privacy "best practices" in their disclosures, handling of personal identifiable information, notifications, and email options. The Summitas Privacy Policy at www.summitas.com/info/privacy outlines our practices. If you have an unresolved privacy or data use concern that we have not addressed satisfactorily, please contact our U.S.-based third party dispute resolution provider (free of charge) at https://feedback-form.truste.com/watchdog/request.